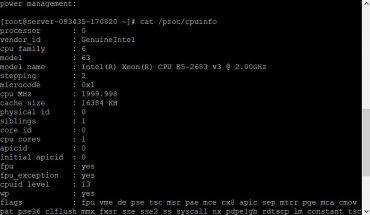
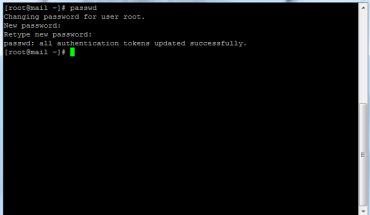
How to check VPS Server parameters with Linux command
When you just bought a VPS but don’t know if the provider has the same configuration as the package you bought, or you want to see how much of the hard drive, RAM and CPU space you can use. commands…