Server security is a topical issue. There are also a number of dangers for public servers such as:
• DDoS attacks
• Brute force attacks
• SQL injections
• Sesson hijacking
• Exploiting vulnerabilities in popular Content Management Systems (CMS) like WordPress
No server is ever 100% secure. However, security experts work daily to uncover and tackle new threats. However, attackers are frequently one step ahead. Therefore, it is important to secure the administrator access to a dedicated Linux server, which is not used for everyday tasks.
Administrator access across different layers
The Secure Shell (SSH) protocol most commonly manages Linux servers. SSH provides encrypted tunnels between server and client, so passwords and sensitive commands are protected. Although the SSH protocol is not uncertain in its current version, security can be increased by extending the default configuration. The Internet Assigned Numbers Authority (IANA), which has an accountant function on certain registrations and it allocates the SSH protocol port 22. Port 22 is the third most widely scanned network protocol on the Internet. Automatic bots and scanners search for the servers that have port 22 open and then try brute force attacks on SSH logins. The attacks can be reduced in three ways.
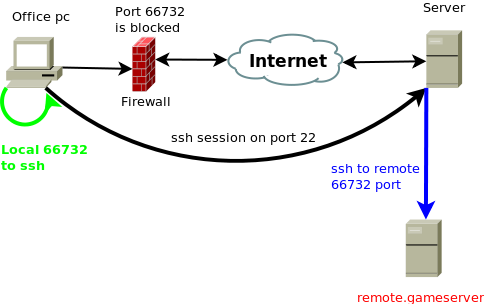
1 . Change SSH ports
By simply changing the port, it will be hard for the SSH daemon to look for a vulnerability in the “right place.” If you select a “non-standard port”, the number of brute-force login attempts will be greatly reduced. In general, bots and scanners go the way with the lowest resistance and effort. This means that an automated bot does not waste its time scanning all 65,000 Transmission Control Protocol (TCP) ports because it knows that there are a thousand other servers where the SSH daemon “listens” on port 22.
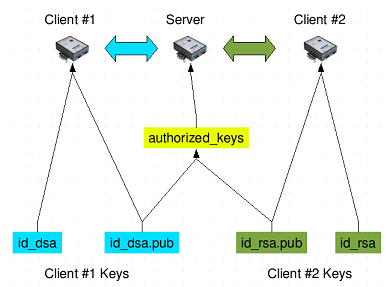
2. Use SSH keys
Asymmetric cryptography methods seem complicated at first glance, but there are usually inside of Linux distributions standard and there are good instructions for creating SSH key additions. Modern SSH keys use asymmetric cryptography to secure and sign digital keys. The aim of this is the transmission and identification of encrypted data. Users should use SSH keys and immediately disable login without SSH keys. Since only the user can identify with the corresponding key, this measure prevents brute-force attacks. Since the key can theoretically also be stolen, users should use a particularly secure password for their private key.
3. Implement ACLs
Another measure to reduce brute force attacks tremendously are access control lists. ACLs are approvals that are bound to a specific object – here the server. The user can use stateful firewalls to restrict SSH access to specific IPs and deny access to all other Internet addresses. For example, bots and automated scanners can no longer connect to the user’s server. To optimize security, ACLs should be applied not only to SSH protocols, but also to all other relevant services.
For maximum secure administrator access, all measures should be applied simultaneously, as a single supplement can not prevent a brute force attack. If the user only changes the SSH port to a “non-standard port”, brute-force login attempts are not prevented, since the changed and new port could also be found. Even the mere use of ACLs does not secure the authentication process by itself. Security experts use the concept of multi-level security, where multiple security layers are stacked together to achieve the best possible coverage.